
In the era of Internet of Things(IoT), wireless communication is getting increasingly popular in everyday life. In the world of IoT devices, ESP32 is a popular low-cost System on Chip (SoC) microcontroller with built-in hybrid WiFi and Bluetooth chips by Espressif Systems. Because of its robust design and ultra-low power consumption, it has become so popular in IoT applications. But when we talk about IoT applications, security in IoT will come to our mind for data safety and secure connection. ESP32 supports X.509 certificate-based mutual authentication for HTTPs, IoT cloud (AWS-IoT, Azure, Google Firebase, etc.) authentication, and data communications. Over the Internet, ESP32 also gives us the data security for stored data into FLASH memory and Boot Sectors to prevent the data from being stolen. Today we talk about the ESP32 security features, mainly related to of Boot sectors. The two main security features on ESP32 are called Secure-Boot and flash security, also known as Flash-Encryption.
What eFUSE Blocks in ESP32?
The ESP32 has a 1024-bits One-Time-Programmable (OTP) memory block. This OTP memory block is divided into 4-block of 256-bits each.
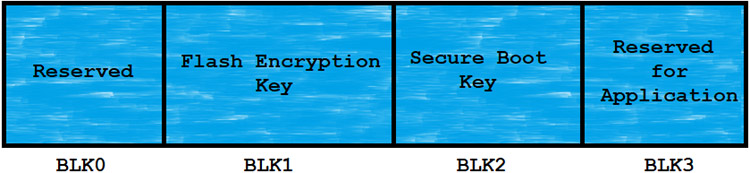
These blocks of memory store the keys of the Flash encryption and Secure Boot. Because of the OTP memory block, there is no software present to read out those memory blocks. One and only ESP32 hardware can read and validate the Security features.
What is Flash Encryption? How to Enable it on ESP32?
ESP32 Flash Encryption is a security feature for the ESP32 provided by the ESP-IDF by Espressif System to protect the flash memory. Flash encryption is encrypting the contents of ESP32’s SPI flash memory and when this feature is enabled, the following types of data are encrypted by default:
- Firmware Bootloader
- Partition Table
- “app” type partitions or Application partitions
- Any partition marked with an “encrypted” flag in the partition table is also encrypted.
In ESP-IDF projects, users can easily enable the Flash Encryption from the project configuration by the
idf.py menuconfig
After open the ESP32 project config menu, now navigate to
“Security Features” --> “Enable flash encryption on boot” --> “Enable usage mode (Development(NOT SECURE))” / “Enable usage mode (Release)”
In flash encryption there are two modes:
- Development Mode: In this mode, the ESP32 flash memory partitions are all encrypted and open for modification and are also accessible to readout flash by the UART.
- Release Mode: This mode is especially recommended for the manufacturing and production stages. In this mode, the readout of the flash by the UART/JTAG is totally blocked and new firmware can only be updated by over-the-air(OTA).
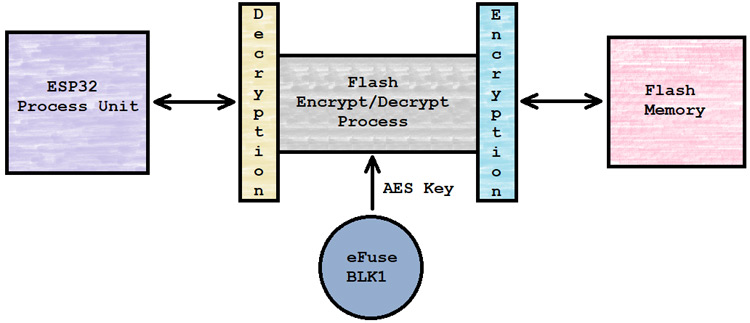
When the flash encryption is enabled, the binaries of the current code flash into the ESP32’s memory as a plain text file. But after completion of the flash process, on the first boot of the ESP32, the device itself encrypted each and every upper mention partition, one by one by using the AES flash encryption key which is stored into the eFUSE-BLK1 at the time of flash. After encrypting the partition the ESP32 device restarted itself and processed with the programmed logic.
The ESP32’s flash execution process decrypts the flash memory data when the ESP32’s execution unit tries to read and for the writing process, the flash execution process encrypts the data before writing into the flash memory.
What is Secure-Boot? How to Enable it on ESP32?
The ESP32 Secure-boot is a security feature, which provides security to run correct applications on ESP32 hardware. When secure boot is enabled, each and every flash memory’s binaries [Software bootloader & Application firmware] are verified before loading with the RSA-3072 based Secure-boot’s signature keys. We can call the Secure-boot a “Guardian of The ESP32”.
For enabling the Flash Encryption, in the same steps we can enable the Secure-boot from the project menuconfig.
“Security Features” --> “Enable hardware Secure Boot in bootloader”
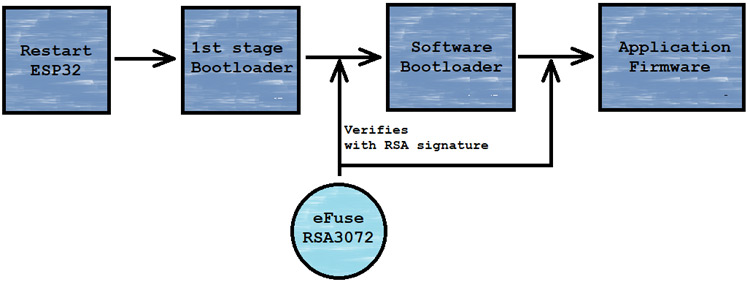
How Secure-boot works?
When the ESP32 device is booted up, then ESP32 hardware’s trusted rom or we said the 1st stage bootloader runs verification with RSA-3072 based secure-boot key on the software bootloader and then the software bootloader verifies the application firmware with the same signature key and start the application.
Conclusion
The ESP32 comes with a secure environment [Secure-boot & Flash-Encryption], which we need to enable while flashing the code. For more security, we need to enable both of them.





