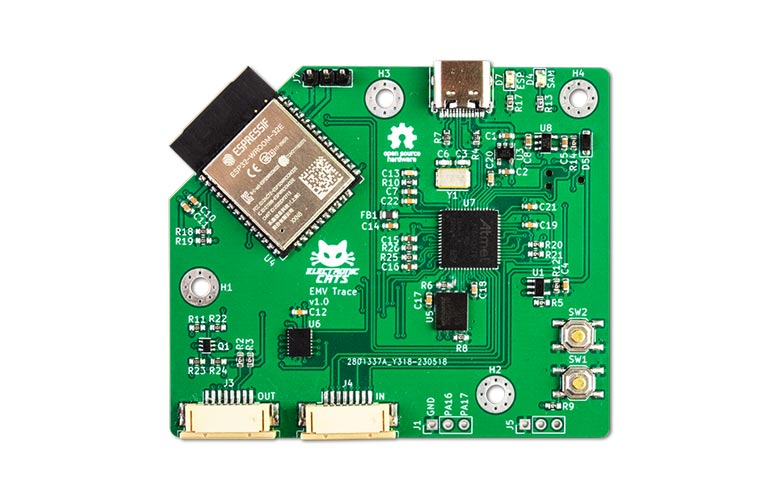
A new hacking, and research tools for EVM protocol analysis has been launched by Electronic Cats, the EMV Trace. This innovative device serves as an intermediary between an EMV card and a payment terminal, enabling the analysis and modification of communication traffic. With a USB-C interface, users can analyse the traffic on a PC, while the built-in ESP32 module allows for remote access. EMV Trace focuses on the application protocol data unit (APDU), which facilitates communication between a smart card's integrated circuit (IC) and a reader. Equipped with connectors, EMV Trace can connect to other boards functioning as a card reader and an emulation card. This unique capability empowers users to monitor, modify, or inject traffic between the two devices, as well as simulate the insertion and ejection of cards to automate security testing.
In terms of communication, EMV Trace offers both USB-C and WiFi connectivity. The ESP32 module enables interaction over WiFi, enabling MQTT message exchange between a card and a terminal. It's worth noting that EMV Trace utilizes the Microchip SAM3S microcontroller, which is also used in the Osmocom SIMTrace board. This similarity allows EMV Trace to function with the SIMTrace 2 software, facilitating the sniffing of traffic between a SIM card and a mobile device based on the ISO 7816 T=0 specification. Electronic Cats, renowned for their development, hacking, and research tools, including the CatSniffer (IoT Scanner) and Hunter Cat (NFC Tool), has made EMV Trace an open-source project. The KiCad design files are available in their GitHub repository, showcasing their commitment to fostering collaboration and innovation in the community.
EMV Trace is currently available for pre-order at a price of $110, with shipping scheduled to commence on August 10th. For DEF CON 31 attendees, there is an option to pick up EMV Trace directly at the conference, offering a convenient way to get hands-on with this cutting-edge device.

